Multi-Factor Authentication & 2-factor authentication
Abstract - The so-called multi-factor authentication (MFA) is also often referred to in practice as two-factor authentication (2FA) and offers secure access to a system through several (often two) independent factors.
Monday, 23. August 2021
How does the login
work without two-factor authentication?
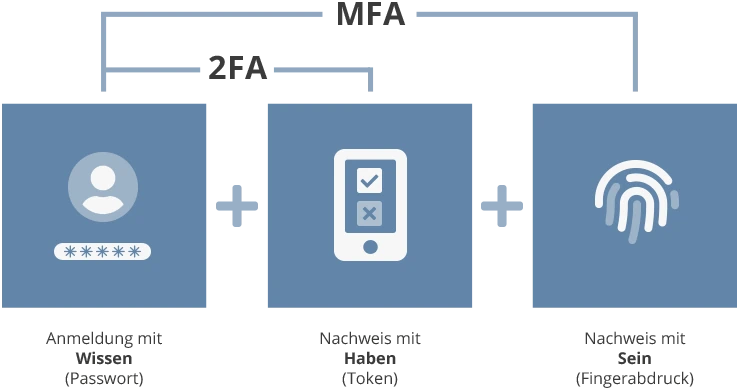
Most access restrictions to IT systems are still based on simple factor authentication: the user password. The password is then a factor for authenticating the user to the system. This authentication factor is assigned to the "Knowledge" category, since it is knowledge that the user must possess in order to successfully log on to the system.
What is two-factor authentication, why is it useful and what does it consist of?
Since knowledge alone is not a sufficient factor to reliably protect IT systems from third-party access, an additional factor should be used for legitimization. This is because knowledge, i.e., the password, can be stolen or guessed, for example, so that access by unauthorized persons is possible. This is where the second factor comes in: by using a cell phone, another factor for secure login can be added by sending an SMS or by retrieving a code in an app, which confirms the identity of the person logging in. This type of authentication factor is categorized as "ownership" because the person who wants to authenticate needs the device on which the second authentication takes place in addition to the password. Consequently, an attacker would have to steal the password and the device that the user has set up for two-factor authentication.
In short:
2FA or MFA refers to the combination of at least two credentials for authentication/logon to a system.
- Online banking or ATM
- Identity card
- Tax return with Elster
- Card payment
- Tax return with Elster
- Online services like PayPal, Facebook, etc.
What are the requirements for implementing multifactor authentication?
Depending on the system, there may be different supported options for the second factor. Major vendors offer a variety of the following options. In principle, you should give your employees the opportunity to decide for themselves which method is most suitable for them. In any case, the company should offer hardware tokens for the key ring, for example, for employees who do not have a company cell phone, do not want to use their own cell phone voluntarily, or simply do not have any of the options available.
Most commonly used authentication methods:
- One-Time-Secrets i.e. one-time passwords so-called OTP or Tans.
- Google Authenticator
- Microsoft Authenticator
- Yubico Authenticator
- SMS (also known as SMSTan)
- Phone call
- Cryptographic keys
- Software certificate (token, key) as file
- HBCI, signature cards, NFC or USB tokens
- YubiKeys
- Fido-Token
2-factor authentication sounds very sensible - so why is it not yet being used across the board?
To put it succinctly, it's all about usability, or convenience. Logging on to systems secured with multiple features can be "annoying," to put it bluntly. Whereas it was otherwise sufficient to enter the password, with activated multifactor authentication, the authentication device must now also be at hand for logging in. For many users, this is a reason not to activate this function. Here, it is important to explain to users how important IT security is and to outline the concrete threat scenario.
For the rest:
The BSI recommends at least two-factor authentication for all online accounts.
On the topic of IT security, you might also be interested in:
How to choose a secure password.
